G-SEC™ Tools and Whitepapers
G-SEC™ offers offensive and defensive IT Security tools, original research, gives regular talks on original topics at security conferences. Here is a summary of Tools, Whitepapers and talks that have been published by our members over the years.
Table of Contents
· Research & Whitepapers
· Free Tools and Proof of Concepts
· Talks and Lectures
Research & Whitepapers
TLS/SSLv3 renegotiation vulnerability explained
This paper explains the SSLv3/TLS renegotiation vulnerability for a broader audience and summarizes the information that is currently available. It includes original research and Proof of concept code.
Updates:
· Updated : Added SMTP over TLS attack scenario
· Updated : Added FTPS analysis
· Updated : New attacks against HTTPS introduced
· Updated : PoC files for TRACE and 302 redirect using TLS rengotiation flaw
Author : Thierry ZOLLER
Download (PDF) : TLS/SSLv3 renegotiation protocol vulnerability
Proof of Concept files:
· Injecting responses into SSLv3/TLS streams : ssl-trace-poc.c
· Downgrading HTTPS to HTTP (!) : ssl-302-inp.c
Read more in this blog post : SSLv3/TLS mitm vulnerability
TLS/SSL hardening and compatibility report 2010
What started as an "I need an overview of best practise in SSL/TLS configuration" type of idea, ended in a 3 month code, reverse engineer and writing effort.
This paper aims at answering the following questions :
· What SSL/TLS configuration is state of the art and considered secure (enough)?
· What SSL/TLS ciphers do modern browsers support ?
· What SSL/TLS settings do server and common SSL providers support ?
· What are the cipher suites offering most compatibility and security ?
· Should we really disable SSLv2 ? What about legacy browsers ?
· How long does RSA still stand a chance ?
· What are the recommended hashes,ciphers for the next years to come
The paper includes two tools :
· SSL Audit (alpha) : SSL scanner scanning remote hosts for SSL/TLS support
· Harden SSL/TLS (beta) : Windows server and client SSL/TLS hardening tool
Author : Thierry ZOLLER
PDF (Full) : TLS Hardening and Compatibility Report 2011
PDF (Condensed) : TLS Hardening and Compatibility Report 2011
Download (With Tools) : SSL/TLS Hardening and Compatibility report 2010
Download (With Tools) : SSL/TLS Hardening and Compatibility report 2011
Related blog post
Free Tools
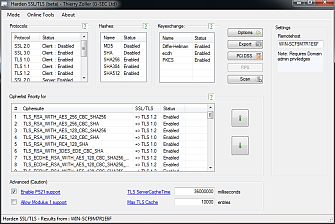
Harden SSL/TLS (beta)
Developed as part of G-SEC's investigation into the "Secure SSL/TLS configuration Report 2010" we developed this little tool.
“Harden SSL/TLS” allows hardening the SSL/TLS settings of Windows 2000,2003,2008,2008R2, XP,Vista,7. It allows locally and remotely set SSL policies allowing or denying certain ciphers/hashes or complete ciphersuites.
This tool specific allows setting policies with regards to what ciphers and protocols are available to applications that use SCHANNEL crypto interface. A lot of windows applications do use this interface, for instance Google Chrome as well as Apple Safari are a few of these. By changing the settings you can indirectly control what ciphers these applications are allowed to use.
Advanced mode
· re-enable ECC P521 mode on Windows7 and 2008R2
· Set TLS Cache size and timeout
Known issues:
· The BETA initialises and sets the OS defaults at startup
Changelog :
· Fixed Protocol initialization on Vista/Seven/2008/2008R2 (Adrian F. Dimcev)
· Fixed TLS 1.1 on Vista/2008 (Reported by Adrian F. Dimcev)
Author :
Thierry ZOLLER for G-SEC
Download: Harden TLS/SSL (beta)
Download: Documentation
Video file
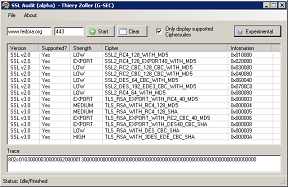
SSL Audit (alpha)
SSL Audit was born out of G-SEC's investigation into the "Secure SSL/TLS configuration Report 2010"
SSL Audit remotely scans web servers for SSL support, unlike other tools it is not limited to ciphers supported by SSL engines such as OpenSSL or NSS but can detect all known cipher suites. It features an innovative Fingerprinting engine that was never seen before.
Fingerprint mode (Experimental)
Included is an experimental fingerprint engine that tries to determine the SSL Engine used server side. It does so by sending normal and malformed SSL packets that can be interpreted in different ways.
SSL Audit is able to fingerprint :
· IIS7.5 (Schannel)
· IIS7.0 (Schannel)
· IIS 6.0 (Schannel)
· Apache (Openssl)
· Apache (NSS)
· Certicom
· RSA BSAFE
Known issues:
· FP on SSLv2 (needs seperated HTTPS request to verify)
· No way to export results
Author :
Thierry ZOLLER for G-SEC
Download: SSL Audit (alpha)
Download: Documentation
Video file
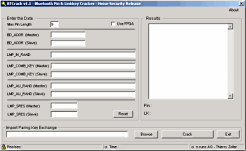
BTCrack 1.1 WindowsBTCrack is the worlds first Bluetooth Pass phrase (PIN) bruteforce tool, BTCrack will bruteforce the Passkey and the Link key from captured pairing* exchanges.
BTcrack was demoed and realeased at Hack.lu 2007 and 23C3 in Berlin, the video of the presentation is available on Google Video .
To capture the pairing data it is necessary to have a Professional Bluetooth Analyzer : FTE (BPA 100, BPA 105, others), Merlin OR flash a CSR based consumer USB dongle with special firmware.
Speed Comparison :
· P4 2Ghz - Dual Core 200.000 keys/sec
· FPGA E12 @ 50Mhz 7.600.000 keys/sec
· FPGA E12 @ 75Mhz 10.000.000 keys/sec
· FPGA E14 30.000.000 keys/sec
Changes :
· 1.0 First release
· 1.1 Intermediate Release
E12 + E14 FPGA Support ( http://www.picocomputing.com)
Splash Screen
Process Priority
Speed increase (+15%)
Author :
Thierry ZOLLER for n.runs AG
Download: BTCrack
Video file
BTCrack 1.1 Open sourceThis is a straight forward open source linux port of BTCrack. Should work with most other unixes too, code is nearly ansi clean, except for strdup().
Author:
Thierry Zoller & Eric Sesterhen
Download : BTcrack OSS
USB write BlockerUsb write blocker is a small tool to block write request to USB devices, which will effectively become READ-ONLY. Requires .NET 2.0 Framework.
Author:
Thierry Zoller for G-SEC
Download: Usbwrite blocker
Omron CommunicatorResearching in the area of payment systems and credit cards we had to reverse engineer the Omron card reader protocol and implement it in software.
Details about the protocol research can be found here, here and here.
Author: Thierry Zoller
Download: Not Available
TLS/SSL v3 session renegotiationThese Proof of Concept files are related to the TLS/SSLv3 renegotiation vulnerability. Please download our whitepaper entitled "TLS and SSLv3 vulnerabilities explained" for more backround information.
Injecting responses into SSLv3/TLS streams : ssl-trace-poc.c
Downgrading HTTPS to HTTP (!) : ssl-302-inp.c
Talks and Lectures
Wireless Security
Hack.lu (2006)
· Press coverage : Symantec, Heise, Network Computing, Tecchannel
Minerva (2006)
· Press coverage: Digital Library Forum
CCC 23C3 (2006)
· Press coverage : Heise, H-online, Magnus, Google Video
Heisec (2007)
· Press Coverage : Heise
IT Sicherheits Forum (2007)
· Information : GAI Netconsult
High Level Security Board (2007)
· Information : none available
M-Vision (2007)
Lecturer : Thierry ZOLLER
Download: Heisec version of the TalkVulnerability research results in Anti-virus and Security Products
Hack.lu (2007)
· Press coverage: Heise, Washington Post, Security Focus, Infoworld
Cansecwest (2008)
· Press coverage: Computerwoche, Le Monde Informatique
Lecturer : Thierry ZOLLER
Download: The Death of AV Defense in Depth ?- Revisiting AV SoftwareResearch into Security Metrics
HLSB (2008)
Lecturer : Thierry ZOLLER
Download: Not available
Note: All trademarks mentioned herein belong to their respective owners.